AsuduVMI
A Stealth Userspace Debugger using Virtual Machine Introspection
AsuduVMI was my Master's Thesis in Informatics: Games Engineering.
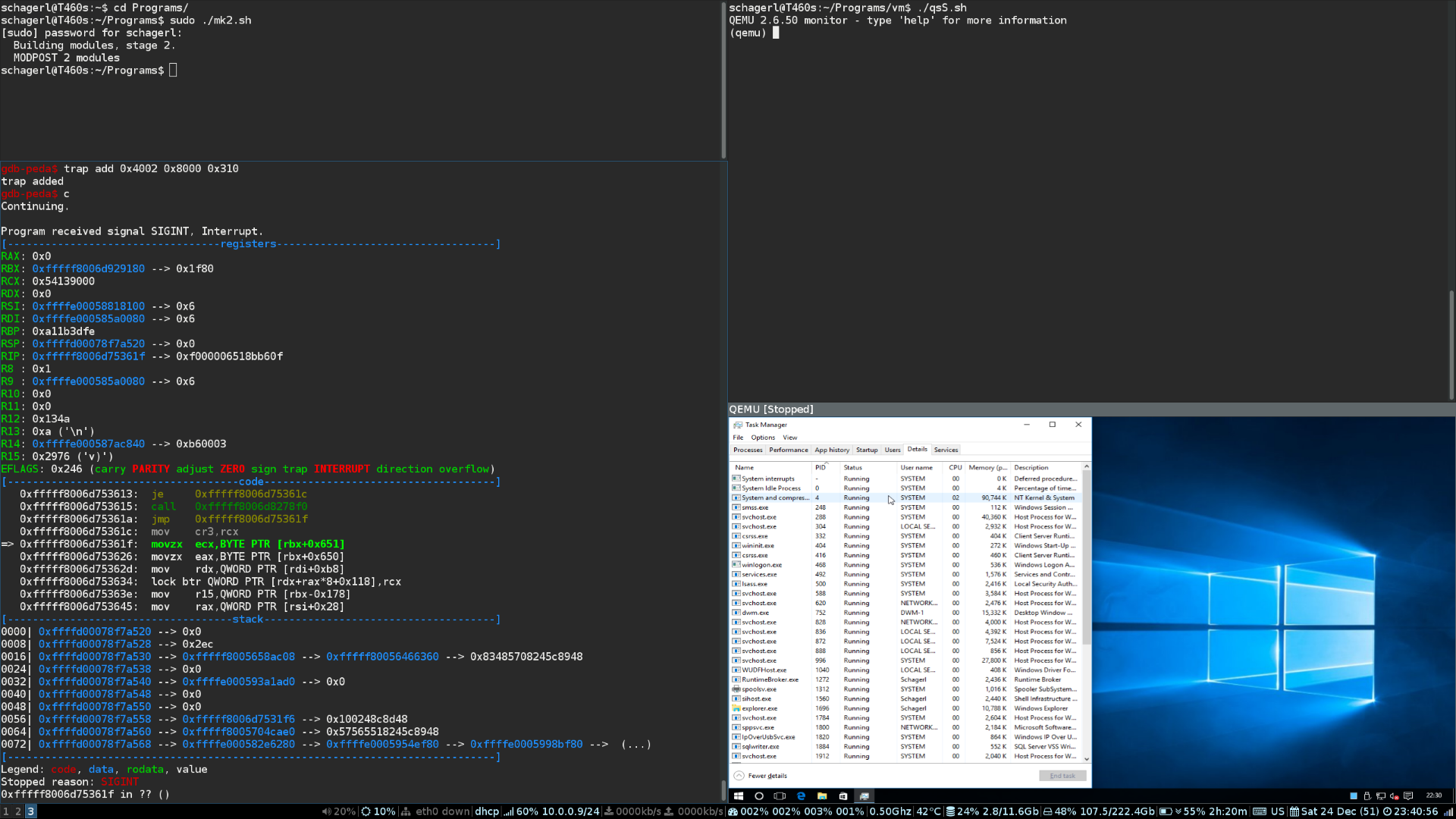
The persistent increase in unique and sophisticated malware requires new debugging methods that are capable of analysing and defending against them. A promising approach is the use of hardware-assisted virtualization technologies in order to perform Virtual Machine Introspection (VMI). This thesis presents the design and implementation of stealth breakpoints and watchpoints that are handled almost completely inside the guest by utilizing new Intel Virtualization Extensions (Intel VT-x) features that had been introduced with the Skylake microarchitecture. It also proposes an algorithm capable of extracting kernel offsets to the Windows process list, that works on all recent Windows versions. Everything is then combined into a framework that brings together all important features required to use VMI for userspace process debugging named AsuduVMI.
Our evaluation confirms the functionality of the process list algorithm across all tested Windows versions. Extensive tests composed of synthetic as well as real world examples show that the proposed techniques are, except from timing, completely invisible to userspace processes in the virtualized system. Contrary to our expectations, conducted benchmarks suggest that the massive effort of moving the logic inside the guest to reduce the number of Virtual Machine (VM) exits might not be worth the performance gain.
We conclude that debugging with VMI is not only feasible but also quite beneficial and with a few more advances it can be a viable solution for malware analysis in the future.